Wednesday, December 22, 2010
Turn Your Phone into a Tricorder
Tuesday, December 21, 2010
Monday, December 20, 2010
New Facebook Profiles Invite New Threat
Security officials from Trend Micro caution that malware creators are taking misusing the buzz made by the latest Facebook profiles to push harmful program on to user's systems with the help of Facebook toolbar.
The toolbar is forged, but is well crafted. The mails appear to have come from Facebook and use the site's template also. The subject of the mail is "Hello dear friend!" and the message is signed by "The Facebook Team".
It reads: "Hi dear Friend. Now you can download the Facebook toolbar. Now it will be easier than ever to share and connect with your friends. Thanks". The message comes with a big green button which says "Download Here", which on clicking, takes to a site serving a file calledfb.exe for download.
As per Trend Micro, this file is actually a variant of the Zapchast IRC backdoor.
Security expert state that Backdoor.IRC.Zapchast installs IRC scripts and configuration files that enable the infected system to be used as a zombie. The infected machine connects to some IRC channels mentioned in the configuration files and is controlled by the hacker. Also, some Zapchast variants come infected a computer virus called Parite.B.
Cristina Buenviaje, Anti-Spam Research Engineer at Trend Micro said that, lately, Facebook brought in some changes to the profile pages of its users which make it easier for users to display their latest activities and to know about their friends. Also, it is not a matter of concurrence that soon after this change, they started getting fake mails from Facebook, as per the news by blog.trendmicro.com on December 9, 2010.
The security experts claim that it has become an expected pattern. Everytime Facebook initiates some changes; the attackers launch mail campaigns that misuse the change and lure users into installing malware.
Facebook has attempted in the past to increase the security level, but as per from BitDefender, an Internet Security Firm, is filled with Trojan horses, keyloggers and other kinds of malware. The viruses could be found in harmful links and other third-part applications.
You can read the full article here.
Saturday, December 18, 2010
Tom's Top 5 Holiday Gifts
Friday, December 17, 2010
Roku Box - Cnet's Gadget for the Holidays
Holiday Tech Scams to Avoid
The holidays can be a dangerous time out there on the internet. Protect yourself by educating yourself and beware of what seems to good to be true, because it probably is. Especially if you heard about it on the internet!
The holiday shopping season is a great time to get tech products at discounted prices, but it also creates a golden opportunity for the Web's scam artists. The FBI, McAfee, the Better Business Bureau and F-Secure are all warning about cybercriminals who will try to take you for a ride this holiday season. Here are their most pertinent warnings and tips for staying safe:
The Infamous Free iPad
Bogus free iPad offers started popping up immediately after Apple's tablet went on sale, and they've since been banned from Facebook. Still, you might see similar offers around the Web, McAfee says, prompting you to buy other products as a condition of getting the free iPad. By now, you should realize it's too good to be true.
Gift Card Scams
That free $1,000 gift card offer you saw on Facebook? Bogus, of course. McAfee says that cybercrooks lure people into giving away their personal information or taking quizzes in exchange for these cards, which never arrive. The information is then sold to marketers or used for identity theft.
The FBI also says to use caution when purchasing gift cards through auction sites or classified ads. These can be fraudulent, and you won't get your money back. Buy directly from retailers instead.
Bogus Auctions and Classifieds
Here's a particularly tricky scheme pointed out by the FBI: On auction and classified sites, fraudsters use their own order forms to get payment details from holiday gift buyers. Then, they charge the victim's credit card and use a stolen credit card to buy the actual item, which is sent directly to the victim. In other words, you'll still get the product, but you might be liable for receiving stolen goods. To avoid this scam, be sure to use legitimate payment services like Paypal instead of providing money directly to the seller.
The feds also warn of a related scam for free or reduced-price shipping offered on auction and classified sites. The fraudsters provide fake shipping labels to the victim, and the product ends up being intercepted in transit, never delivered to its destination.
Malicious websites
For cybercriminals, spamming Google with bogus holiday gift pages is a yearly tradition. These pages could be loaded with malware or payment forms intended to steal your identity. F-Secure has created a list of what it thinks will be the highly targeted search terms this year, including Kinect for Xbox, Call of Duty: Black Ops, Amazon Kindle and Apple iPad. Visit retailers' websites directly when possible, use Internet security software if you must and always check for "https" in the URL bar before ordering online to ensure that the page is secure.
Wi-Fi Hackers
Public Wi-Fi networks will get a workout this holiday season as people travel, McAfee notes. This is especially true with Google offering free Wi-Fi on domestic flights from three major airlines. Check out our security tips from Google's free Wi-Fi offer at airports last year, most of which are still relevant in the skies. Number one tip: Avoid shopping and paying bills over a public network.
The read the full article from PC World click here.
Fake DHL / FedEx Delivery Email Messages
Recently, security researchers at AppRiver (security firm) have warned of a fake malware infected DHL delivery status e-mails that are targeting innocent internet users.
The "From" column of the e-mails is spoofed as if it had come from "DHL Services" and the complete content of the message is written in Spanish. These emails are quite different from all other DHL spoofs as they exploit a real DHL email template, which comprise the company's logo, color schemes, images, and contact information.
These fake e-mails states that a package could not be delivered on time due to unclear or badly written shipping address. The e-mail further informs recipients that the parcel can be collected from the local post office. To collect the parcel, the e-mail asks the users to carry along a print of the shipping label enclosed in the attachment.
The shipping label attachment is named Etiqueta_ID#####.zip (# being a random digit) and encloses a folder with a malicious .exe file. The file contains a fake Excel document icon, which installs an Oficla variant. The Oficla family of malware is called droppers. As the name suggests, their main aim is to penetrate into systems and drop malware that can further damage the system.
Commenting on the issue, Fred Touchette, Security Researcher at AppRiver stated on his blog post that, he was not sure that who would like to get into all of these troubles by clicking on several links and attachments, but one thing he was sure of is that, this trick works. He further said that, he could only presume that those files were foldered and zipped to avoid detection by anti-virus software, which doesn't check that thoroughly, as reported by AppRiver on October 25, 2010.
Finally, users can apply their common sense approach and keep in mind the following suggestions to avoid falling prey to such malware attacks. First and foremost, if the user doesn't speak Spanish, he should immediately delete from their inbox. In case, if the user speaks the language, but not expecting some DHL shipment, then also he should immediately delete the e-mail.
But in case, if the user is expecting a shipment from DHL and speaks Spanish, then he should think for a while regarding the poorly written message and understand that a reputable company would not sent such a badly written thing or file attachment like this (via e-mail).
You can read the original article here.
Monday, December 13, 2010
Email Message Hoaxes - Don't Be Afraid
 the know” who has information about a major virus on the horizon. These messages can almost always be ignored. The email message you received from the “reliable source” asking you to forward it on is the “virus” itself. We will talk about these messages in more detail during next week’s IT classes.
the know” who has information about a major virus on the horizon. These messages can almost always be ignored. The email message you received from the “reliable source” asking you to forward it on is the “virus” itself. We will talk about these messages in more detail during next week’s IT classes. Dave's brother is a very advanced programmer who does
computer work for a living and has a high up status with Microsoft. He
doesn't send these if they aren't real. If he says this is for
real, it for sure is. Be aware.
VIRUS COMING !
Hi All,
I checked with Norton Anti-Virus, and they are gearing up
for this virus!
I checked Snopes, and it is for real. Get this E-mail
message sent around to your contacts ASAP.
PLEASE FORWARD THIS WARNING AMONG FRIENDS, FAMILY AND
CONTACTS!
You should be alert during the next few days. Do not open
any message with an attachment entitled 'POSTCARD FROM
HALLMARK,'regardless of who sent it to you. It is a virus which opens A
POSTCARD IMAGE, which 'burns' the whole hard disc C of your computer.
This virus will be received from someone who has your e-mail
address in his/her contact list. This is the reason why you need to
send this e-mail to all your contacts. It is better to receive this
message 25 times than to receive the virus and open it.
If you receive a mail called' POSTCARD,' even though sent to
you by a friend, do not open it! Shut down your computer immediately.
This is the worst virus announced by CNN.
It has been classified by Microsoft as the most destructive
virus ever. This virus was discovered by McAfee yesterday, and there is
no repair yet for this kind of virus. This virus simply destroys the
Zero Sector of the Hard Disc, where the vital information is kept.
COPY THIS E-MAIL, AND SEND IT TO YOUR FRIENDS.
REMEMBER: IF YOU SEND IT TO THEM, YOU WILL BENEFIT ALL OF US
Wednesday, December 8, 2010
Create & Mail PDF files from Excel 2007
A new feature of Microsoft Excel 2007 (with Microsoft Office Service Pack 2 installed) is the
ability to create and mail Acrobat Reader PDF files. If you do not wish to install Microsoft
Office SP2, you can install just the add-in. You can download it here :
2007 Microsoft Office Add-in: Microsoft Save as PDF
After the add-in is installed you can use the code below or do a manual Save As PDF.
Office Button >Save As ….PDF
Office Button >Send ….PDF
Note: In Excel 2010 the big round Office Button is replaced by File
Tips / warnings :
1) If you have also installed Acrobat Reader you can change OpenAfterPublish in the code to
True to open the PDF file after you create it.
2) The mail code example is not working with Outlook Express or Windows Mail.
3) If you set OpenAfterPublish in the code to True then you can do a manual send in
Acrobat Reader (also with Outlook Express or Windows Mail).
4) If there is no printer installed the add-in will not work. You only have to install a printer driver
of one of the printers in the default printer list, you not need a real printer to use the add-in.
5) When you use a hyperlink to another place in the workbook or if you use the Hyperlink
worksheet function the hyperlinks are not working in the PDF.
If your workstation still have Microsoft Office 2003 and you would like the upgrade to 2007 please create a Track-It work order requesting an upgrade.
Tuesday, December 7, 2010
Are the feds about to take over the internet?
More News Coming on New Life Form
"cdmann: More on “new” bacterium from Cali's Mono Lake! “Arsenic and Meaning of Life,” 1 – 3 pm ET (18:00 GMT) on NASA TV http://go.nasa.gov/ax5PCk"
--http://twitter.com/cdmann/status/12189669785608192
Monday, December 6, 2010
A Windows XP Tip: The Startup Folder
A quick way to boost your computer's performance is to reduce the number of applications it runs when starting up. Some programs, such as anti-virus and hardware utilities, need to be run automatically, but an overabundance of startup applications can overwork a computer and use up too much memory.
The easiest way to keep programs from running automatically is to remove them from the computer's Startup folder:
1. First double click My Computer from the desktop, or select it from the Start Menu.
2. Double click the hard drive (default C:\).
3. Open the Documents and Settings folder.
4. Open a specific user account folder, or select All Users.
5. Double click the Start Menu folder.
6. Select Programs.
7. In the Programs folder, find the Startup folder and double click.
Any shortcut within this folder will launch a program automatically on startup. To take it off the list of startup applications, simply delete the shortcut. No worries because you are not actually deleting the program but simply stopping the program from starting automatically (on boot).
Sunday, December 5, 2010
How many astronauts is too many for NASA?
 |
| Goodbye Space program |
Just think, back in 1968 and 1969 even as the Vietnam war was engaged, college campuses exploding with protests and leading politicians being gunned down our nation remained committed and capable in directing it's limited scientific resources & energy to going to the moon. Today with technology exploding all around us, our nation has had to resort to canceling the space shuttle program while at the same time canceling future man space exploration. That is unless the Russians are willing to let one of our astronauts hitch a ride on one of their spacecraft (for a price of course).
I was 5 years old when our nation first landed on the moon and 9 years old when our last astronaut, Gene Cernan left the moon (Apollo 17). Unless something drastically changes, I will probably never get to see another human being in deep space and I fear for our children as well. What has happened our nation's vision of being the leader in exploration? Exploration and personal growth provides people with something to be proud of. Being a truly unified nation is much more then war and taxes.
To learn more about the fate of many of our astronauts check out the following article.
NASA: How many astronauts is too many for NASA? - OrlandoSentinel.com
Saturday, December 4, 2010
Let's Talk Tech
 |
| Let's Talk Tech |
Join the West Chester Tech discussion at http://wctech.46.forumer.com. Only here can you easily discuss all things tech with your co-workers in an open and fun way. Have fun, be honest but be respectful as well. I am not sure about everyone else, but I am quite sensitive so be nice.
You will always be able to find a link to the WC Tech Forum on the right side of our tech blog.
Friday, December 3, 2010
New Life Form Announced : Through the Wormhole : Science Channel
The Science Channel is one of the few channels I actually watch regularly anymore. The channel and their corresponding webpage are both great places to keep up on the latest science news. As I mentioned earlier NASA has discovered a new "life form" and of course the Science Channel has jumped on this news by announcing a special episode of "Through the Wormhole" on December 4, 2010 at 8pm, Be sure to check it out dedicated readers.
| (From the Science Channel) |

NASA has discovered a strange bacteria living deep in a California lake that can survive on arsenic and can even grow by incorporating the element into its DNA and cell membranes.
The finding not only presents the possibility that alternative life forms can exist, or once existed, on Earth. It also has deep implications for the search for life beyond Earth. It also muddies the waters for scientists refining techniques to identify alien life, if it exists.
Get the whole story.
Don't miss a special presentation of the "How Did We Get Here?" episode of Through the Wormhole with new footage about NASA's discovery. Tune in on Saturday, December 4 at 8PM E/P.
Expand Your Viewing Options
With the quality of the content on conventional TV decreasing with each passing year, do yourself a favor and check out some of the great offerings on the internet for educational and fun content. I will cover many more of these options in a detailed article soon.
One of my favorite weekly offerings on Revision3 is "Tekzilla". Check it out friends.
Weekly Tip: Locking your Computer
Keeping your data secure is critical. Allowing others access to your computer is unwise to say the least. Think of walking away with your computer “open” in the same way as walking away with your open purse or wallet unattended in a public place. Now I am fairly certain most people would never intend to leave their open purse or wallet unattended and your computer should be treated in the same manner.
It is very easy to “lock” your computer when you get up from your desk to walk away. For example, lets say you want to walk away from your desk, and deliver a hot cup of coffee to your IT Manager. Here are some easy directions to lock your PC while you deliver that much needed cup of coffee:
1. via the keyboard
The easiest way to lock Windows XP is by simply pressing the Windows logo key and the letter L (for Lock) on a Microsoft Natural Keyboard or any other compatible keyboard that includes the Window key. Doing so will pop up the Unlock Computer Password box.
2. via a Shortcut.
If you don't have a keyboard with a Window key or simply don't like the keyboard method, then here's how you can make a desktop shortcut to lock your computer.
Right click an empty area of your desktop, choose New/Shortcut and enter this line as the command line:
rundll32.exe user32.dll, LockWorkStation Click. Next. Name the shortcut whatever you prefer and click Finish. That's it. Pretty simple wouldn't you say.
There are other ways to lock your workstation such as simply pressing the [ctrl] [alt] and [delete] keys and selecting "lock computer" so please do yourself a favor and lock your computer when you step away from your work area. The data you save may be your own!
New Life Form Discovered
You can learn more about NASA's latest discovery here.
Epic Mickey Review & Rating | PCMag.com
To learn more check out PC Magazine's article at Epic Mickey Review & Rating PCMag.com.
Thursday, December 2, 2010
Windows 7 for Sandi
Watch Out For E-Card Trouble

Staying safe online is always a challenge and with the holidays the virtual Grinch's surround us along with the cheer. Lets face it, everyone likes receiving greetings cards and the hackers know this. That is why it is critical for all of us to protect not not only ourselves, but our network as well. The problem is that it can be difficult to spot these potential assaults because they come in so many forms and it seems as though new ones are being created daily. E-cards received in your email, like the popular “postcard from Hallmark virus” is one such scam that is circulating the internet these days, and here is what you need to know about it.
Postcard From Hallmark virus - What Is It?
This particular hoax is merely an email that is being sent that warns the recipient of the worst email virus ever. It tells you that if you receive an email telling you that you have a postcard from Hallmark that this email is carrying the worst virus ever and that this was confirmed by Snopes.com. The virus is supposed to burn your entire hard drive. While it is important to remember that emails can carry viruses and that you should always be careful, this particular email is a hoax. This email itself is a problem in the sense that it causes human hysteria, although your computer is actually safe!
How About Other E-Cards I May Receive In My Email?
Quite simply never open e-cards, no matter the time of the year. E-cards have a terrible history of exploiting users who open them, resulting in viruses, trojan horses and worms.
Our in-house computer security training on December 21, 2010 will address this issue in more detail.
Monthly Gadget Review
This holiday season the hot gadget is the Samsung Galaxy Tablet. At 7” x 4” as compared to the Apple I-Pad’s larger frame of 9” x 7” the Galaxy is a much more mobile device then the I-Pad, weighing in at about half of the I-Pad. This article is not meant to actually compare the two devices so that is all you are going to hear about the Apple I-Pad. (I actually can’t help myself a little later in the article.)
Samsung’s Galaxy tablet runs on Android 2.2 software which is becoming one of the most popular mobile device OS’s (operating system) today. The big four carriers (ATT, Verizon, Sprint and T-Mobile) all have different plans for the Galaxy so you need to be aware of this if you are thinking about it. Personally I believe the most fair plan is Verizon Wireless for 20 bucks a month. With this plan you get 1GB of traffic over their network, but the best part is that you are not locked into a contract and you can cancel the plan at any time. After the plan is cancelled with Verizon Wireless, you simply treat the tablet like a laptop, using it’s wireless connectivity to access any wi-fi network.
The device is sturdy and because it is about the size of a trade paperback it is as mobile as a book making it very easy to travel with. If I carried a purse (which I don’t) you could easily store it there as well! 
Now on to the fun stuff. What can you do with it once you have one? Android software was initially developed by Android Inc. and eventually purchased by Google in 2005. Android has been slowly developing and becoming more popular with mobile devices and has truly become a big player in the market. The operating system is dependable and easy to learn, although there are those who claim that it is a too “techy”. Android software is “community-based firmware” which means that it is open source allowing for programmers to easily develop software for any device running Android. What this means is there are always plenty of useful and fun apps (or applications) for the device.
In addition to surfing the web with various browsers of choice (Android Browser, Firefox and Dolphin, with Chrome on the way) you can get your social networking on with Facebook, Twitter, Linked-In, Goodreads and more. Watching video from services such as Youtube is flawless as well.
If you are a book reader (like me) and you have been thinking about e-book readers like the Amazon Kindle or Barnes & Noble Nook, look no further that this device. The Galaxy has great apps for both which work great. I actually have had a Nook for about a year, and after a day or two with the Galaxy Tablet I was able to retire it (giving it to one of my sons of course) and use the galaxy for this purpose as well. The display is easy on your eyes when you are reading and at night you won’t even need a night light because of the screen!
With the Galaxy Tablet you can remain in touch with work (if you want to) because it is easy to access your corporate email, calendar and tasks on your device. At the same time you can enjoy social networking sites, plenty of games, internet sites, HD video, music and more all on the same small 7” tablet.
Unlike the I-Pad, Android supports Flash which is important when browsing many websites as well as video formats such as XviD and DivX.
With an additional 1.3MP camera in on the front of the device, you will be able to engage in video chats, something you cannot do with an iPad. Wi-Fi and 3G connectivity will take care of your browsing needs. Battery life of Galaxy tablet is impressive to, with the device able to deliver up to seven hours of movie playback without charging.
As I noted above there are several price points, with Verizon Wireless probably being the best choice because you can actually cancel the service contract resulting in no monthly cost.
You can learn more about the Samsung Galaxy Tablet here.
To lean more about Android click here.
Wednesday, December 1, 2010
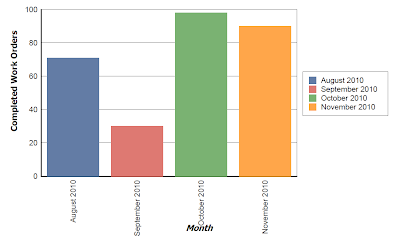
A Big "Track-It" Thank You
Viruses, Worms and Trojan Horses Oh My!
- Passwords
- Viruses
- Trojan Horses
- Worms
- Spam
Please make sure to sign up today for either the morning session starting at 10:00am or the afternoon session at 1:00pm. If anyone has any questions please contact me at cdmann@west-chester.com.
Droid Test
Our Own Tech Blog Opens!
 |
| Posing for State Tech Magazine |
I will work hard to keep everyone up to date with the latestet technology trends as well as gadget news. Also, and more importantly I will strive with this blog to keep everyone up to date with virus, spam and other security news in order to keep all of us safe, at least virtually.
In today's virtual world we all need to stay alert to security concerns, technology trends and software options that seem to expand each and every day. My goal is to provide some useful information as we journey through this new tech world together and just may have a little fun along the way.